Computational Analysis of Plausibly Post-Quantum Secure Recursive Arguments of Knowledge
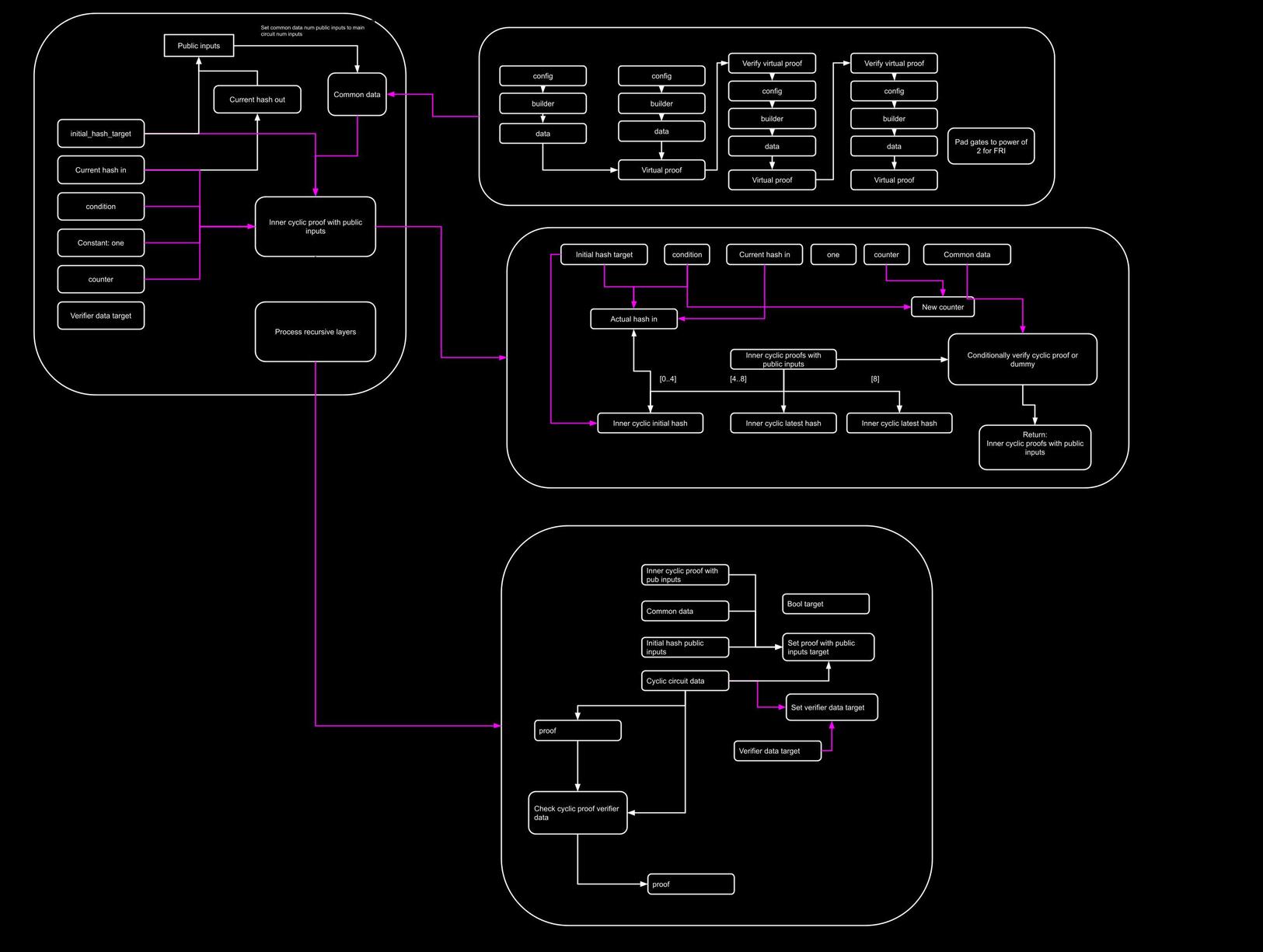
Explore quantum-resistant zero-knowledge cryptographic proofs with Plonky2. This project implements a prover/verifier pair for a recursive computation chain, ensuring computational integrity across large-scale hashing operations. Featuring recursive proof compression for efficient scaling, it demonstrates advanced circuit design and recursive hash verification.
